
FREE DDoS Protection
- 1Tbps+ Protection
- Included with VPS & Dedicated Servers
- Active Filtering
- Instant Activation

At InterServer, we're committed to safeguarding the online presence of our customers. Distributed Denial of Service (DDoS) attacks are one of the most persistent and dangerous threats facing websites today, and we're proud to offer *free DDoS protection* for all our customers. This blog post takes a deep dive into the advanced technical processes and tools we use to detect, mitigate, and neutralize DDoS attacks in real time.
A DDoS attack involves overwhelming a server, network, or website with a flood of malicious traffic. These attacks are designed to exhaust resources, disrupt normal traffic, and render services unavailable to legitimate users. With the ever-evolving sophistication of DDoS attack techniques, from volumetric floods to application-layer attacks, robust protection is no longer optional-it's essential.
Our DDoS defense starts with an array of proprietary monitoring tools. These tools continuously analyze incoming traffic for unusual patterns, such as:
1. Traffic Spikes: Sudden surges in requests from multiple IP addresses.
2. Protocol Anomalies: Irregularities in packet structures that don't conform to expected norms.
3. Repetitive Behavior: Excessive requests to specific endpoints or resources.
These tools use machine learning algorithms and heuristic-based detection methods to distinguish between legitimate traffic and potential malicious activity.
When an attack is identified, our system categorizes it based on several parameters, including:
1.Type of Attack: Is it a volumetric flood, protocol-based attack, or application-layer exploit?
2. Traffic Intensity: How much bandwidth is being consumed?
3. Target Identification: Which IP or resource is under attack?
The system operates in real-time, ensuring that threats are identified and acted upon in milliseconds.
Once an attack is detected, malicious traffic is automatically redirected to *Path.net*, a global leader in DDoS mitigation services. Path.net's infrastructure is designed to absorb and filter even the most aggressive DDoS attacks. Here's how the process unfolds:
1. Redirection: Attack traffic is rerouted to Path.net's scrubbing centers via BGP (Border Gateway Protocol) announcements. This ensures that only malicious traffic is diverted, while legitimate traffic flows normally.
2. Path.net uses high-capacity filtering systems that employ advanced techniques such as:
Rate Limiting:Throttling excessive traffic to manageable levels.
Signature Matching:Identifying and blocking known attack patterns.
Behavioral Analysis:Differentiating bots from humans based on traffic behavior.
3. Clean Traffic Forwarding: After filtering, legitimate traffic is sent back to InterServer's network, ensuring uninterrupted service for our customers.
Once the attack subsides, our system automatically reverts traffic back to its normal routing path. This seamless transition ensures minimal impact on performance and availability.
1. Comprehensive Coverage: From volumetric to application-layer attacks, our system handles a wide range of DDoS threats.
2. Real-Time Response: Automated detection and mitigation processes operate in milliseconds.
3. No Impact on Legitimate Traffic: Advanced filtering ensures that genuine users are never affected.
4. Scalability: With Path.net's global network and our robust infrastructure, we're equipped to mitigate even the largest DDoS attacks.
5. Cost-Free Protection: Unlike many providers, we offer this advanced protection to all customers at no additional cost.

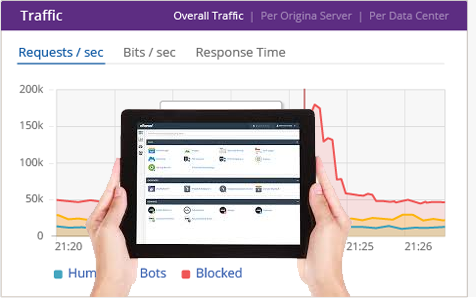
Dedicated Servers are protected with our DDOS protection service for attacks. In the event of a DDOS attack, InterServer will identify the source and destination of the attack and apply appropiate filters.

Keep your websites and web applications online during a DDOS attack.
Currently under attack? Please contact us ASAP for solutions.
On-demand protection can handle almost any size attack. UDP floods, ICMP (ping) floods, SYN floods, NTP Amplification, HTTP Floods, and more. The scrubbing service will automatically detect and block the bad traffic.

Prevent service disruptions.

Passive defense when not under attack. No slow down in speeds.

Keep your business running even when under attack.

The size of the attack will not increase your bandwidth utilization.
We also have full time DDOS protection on floating ips . Protection powered by path.net. With ability to move the ip to any server within a region. Configure custom firewall rules for more advanced scurbbing and control.